PicoCTF Trivial Flag Transfer Protocol writeup
Hi, it’s me again, today i will write about the Trivial Flag Transfer Protocol.
Hi, it’s me again, today i will write about the Trivial Flag Transfer Protocol.
Hmmm… we need to get the file to our local machine and analyze it.
wget https://mercury.picoctf.net/static/fb24ddcfaf1e297be525ba7474964fa5/tftp.pcapng
file tftp.pcapng
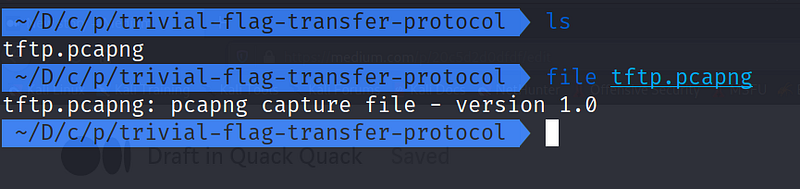
And we get the file, it’s a network capture file, i will use WireShark to see what it contains
wireshark tftp.pcapng
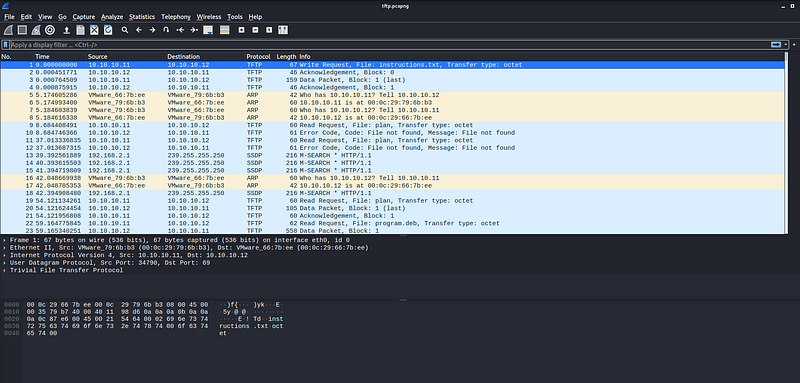
There’s a lot of stuff going on here, isn’t it? But most of the network traffic here are TFTP. I gotta be honest that i’ve never used TFTP before, so why don’t we take a brief look on Google to see what TFTP really is? can we pet it?
After a while of researching, i found out that in a nutshell TFTP is a file transfer protocol using UDP without the need of authentication and data encryption. Though UDP is not reliable but the protocol itself is reliable due to implementing ACK packet and it quite simple. Indeed, it works like this:
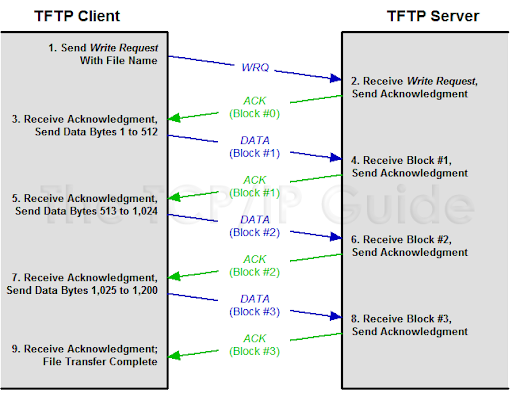
Simple, isn’t it?
Then i did some filter on the capture frame to see what were sent and received
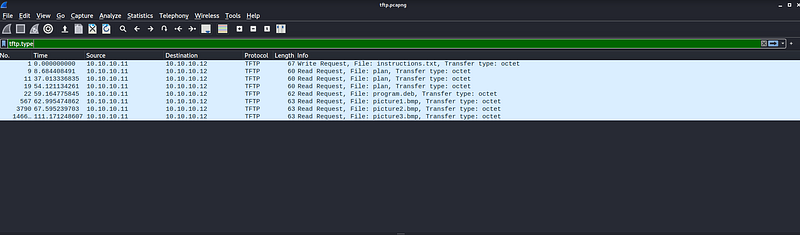
tftp.type
We can see the files were sent in this order “instructions.txt”, “plan”, “picture1.bmp”, “picture2.bmp”, “picture3.bmp”. Now let’s export all of them to see what they contains by clicking File -> Export Object -> …TFTP
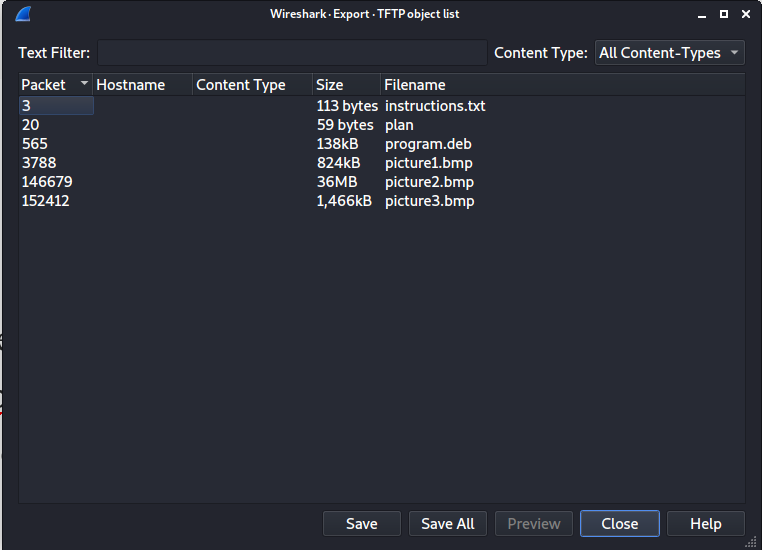
Then we can click Save All → Choose Folder to save → Click OK. Now we have got all the files we need, let’s dig in the same order all the files were sent. The first one is “instruction.txt”.
cat ./instructions.txt
And we get
GSGCQBRFAGRAPELCGBHEGENSSVPFBJRZHFGQVFTHVFRBHESYNTGENAFSRE.SVTHERBHGNJNLGBUVQRGURSYNTNAQVJVYYPURPXONPXSBEGURCYNA
What is this? those text are just none sense. Maybe it’s encoded? Let’s me introduce you to the ROT13 “rotate by 13 places”. Why Rot13? i gotta be honest that i don’t know, it’s just my intuitive when it comes to CTF, it should be base64 decode or Rot13 decoding.
After doing a Rot13 decode (you can go to https://rot13.com to decode it), we get
TFTPDOESNTENCRYPTOURTRAFFICSOWEMUSTDISGUISEOURFLAGTRANSFER.FIGUREOUTAWAYTOHIDETHEFLAGANDIWILLCHECKBACKFORTHEPLAN
Now it makes sense isn’t it? let’s add some space into the decoded text, now we have
TFTP DOESNT ENCRYPT OUR TRAFFIC SO WE MUST DISGUISE OUR FLAG TRANSFER. FIGURE OUT A WAY TO HIDE THE FLAG AND I WILL CHECK BACK FOR THE PLAN
Ok, it says what it means, “I will check back for the plan” and we have the “plan” file which we got earlier from the pcapng file, remember? Then let’s dig in that file
cat ./plan
And once again we get some nonsense text
VHFRQGURCEBTENZNAQUVQVGJVGU-QHRQVYVTRAPR.PURPXBHGGURCUBGBF
Yep, i did Rot13 decoding again, and we got
IUSEDTHEPROGRAMANDHIDITWITH-DUEDILIGENCE.CHECKOUTTHEPHOTOS
With some spaces added, it just make sense :)
I USED THE PROGRAM AND HID IT WITH-DUE DILIGENCE. CHECKOUT THE PHOTOS
“The program”? we also get a program which is “program.deb” from the traffic file, i know it’s a bad idea but i’m gonna install the program
sudo apt-get install ./program.deb
If you pay attention to the log on your screen while installing the file says “Note, selecting ‘steghide’ instead of ‘./program.deb’” which tell you the actual program name is steghide. Now we gotta check out what steghide is and how to use it :((. http://steghide.sourceforge.net/

Hmmm… it supports hiding data in bmp file, no doubt the flag must be in the .bmp file which we got earlier. Well, if you also don’t know what bmp file is (as i am at that point :V ). It’s a picture file format, and bmp stands for “Bitmap Image format”. Alright, let’s go back to the steghide program, as the documentation says, we can reverse our flag by using this command, but it requires a password:
steghide extract -sf <fiflename> -p <password>
Do you remember the decoded text in the “plan” file which we got earlier? It says “WITH-DUEDILIGENCE”. What if “DUEDILIGENCE” is our password? There’s only one way to know
steghide extract -sf ./picture1.bmp -p “DUEDILIGENCE”
We got “steghide: could not extract any data with that passphrase!”. Let’s try it with the other two images
steghide extract -sf ./picture2.bmp -p “DUEDILIGENCE”
Still, we got nothing, but i got luck with the last one :)
steghide extract -sf ./picture3.bmp -p “DUEDILIGENCE”
The Console output with wrote extracted data to “flag.txt”. it must be the flag here :). Let’s cat it.
cat ./flag.txt
And the console output is: picoCTF{h1dd3n_1n_pLa1n_51GHT_18375919}
That’s it, it tooks me about 2 3 hours to get familiar with the Wireshark and get some knowledge of TFTP. Thanks a lot for reading my post and see you next time :)