PicoCTF writeup MarcoHard WeakEdge
Find the hidden flag inside pptm file
Introduction
Hi, this is my first post on Medium, today i found something quite interesting which is why you are here, it’s solving the CTF puzzle. Does it sound weird that i call it “puzzle”?
A bit about me
Ok, briefly about me. I’m a developer with 2 years of experience, which is not a lot but quite a bit to start. I think it’s enough about me since you are here for the CTF challenge, right? So let’s get started.
The challenge
I will use Linux (Kali Linux) because i’m learning Linux, if you use Windows or Mac then it’s fine, just get the alternative tools to get the job done.
Objective: find the flag which is hidden inside the “Forensic is fun.pptm” file.
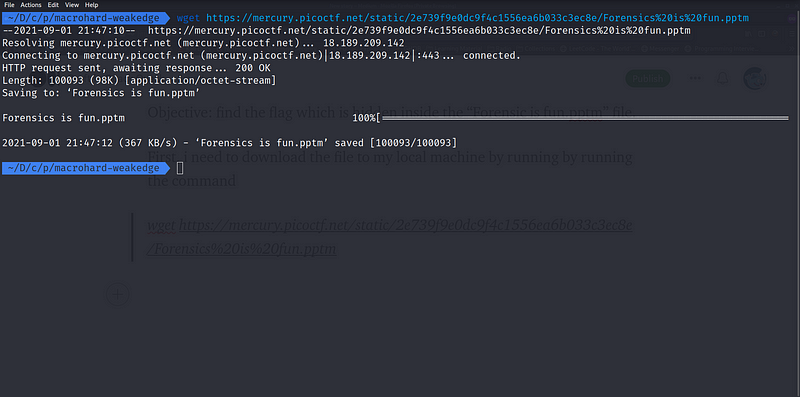
First, i need to download the file to my local machine by running by running the command
wget https://mercury.picoctf.net/static/2e739f9e0dc9f4c1556ea6b033c3ec8e/Forensics%20is%20fun.pptm
So, what is it?
file ./Forensics\ is\ fun.pptm
Let’s google what a .pptm file is?
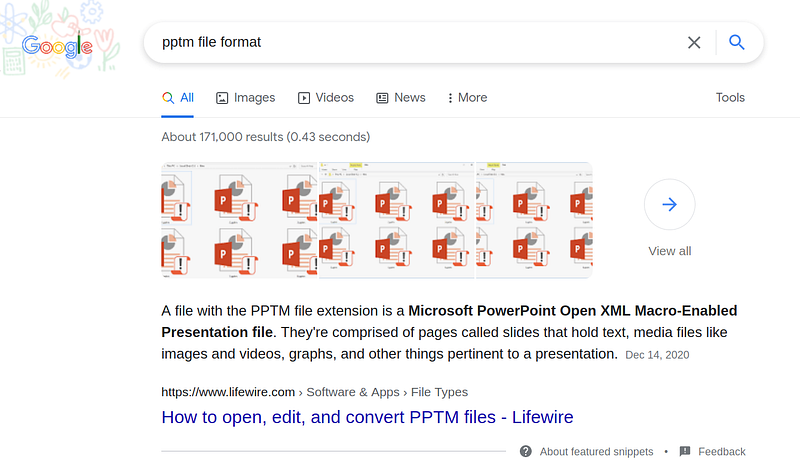
Aha, it’s simply a PowerPoint file with Macro-Enabled, in case you don’t know what macro is, it is a feature which let you write code to automate tasks. And that’s also a “Aha” moment for me, i thought it must be the key here since the title also contains the phrase “macro”. So, let’s open the file using LibreOffice7.2 and see what the file’s macro contains.
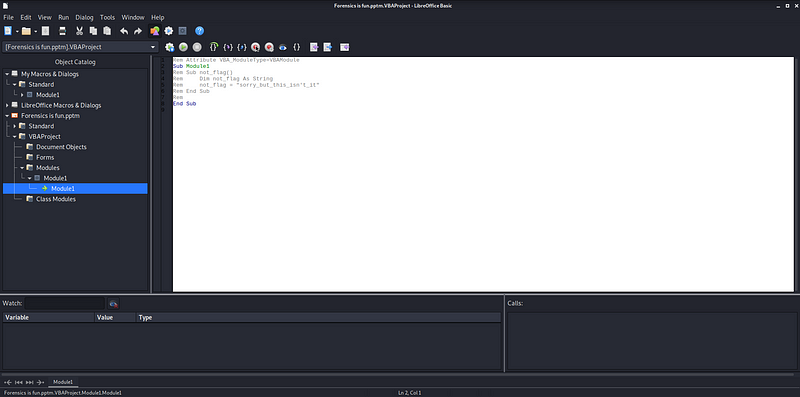
Yup, i was so naive and thought that the flag should be in the macro Content, but nothing was there, it’s just the author tricking us into thinking the flag is in the macro content. Ok, we got to an end, where the flag could be?
Then i search on Google about “hidden macro” of pptm file format but couldn’t find what we need, so i research again on the pptm file format itself, not the “hidden flag” it could contains but the file format itself.
I got luck and found this link about pptm file format, in short either the ppt or pptm file is able to be decompressed by changing the extension to .zip and use tools to unzip the file.

Let’s unzip it
unzip ./Forensics\ is\ fun.pptm
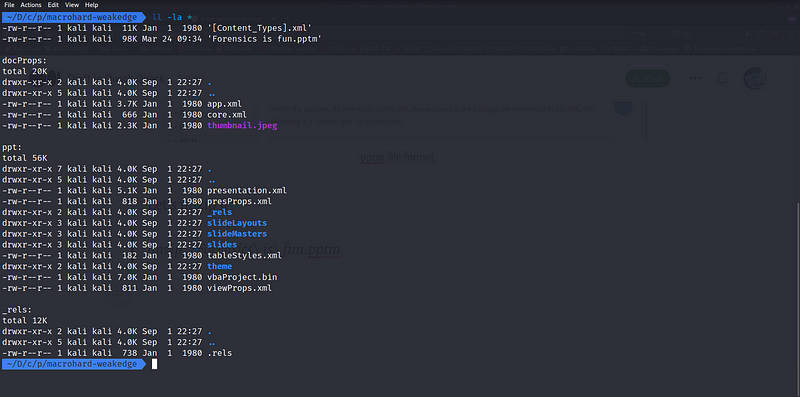
We get a bunch of file, our PowerPoint file contains mostly .xml and .rel file. So let’s find all the file which is not .xlm and .rel
Here i use the tool fuzzy finder to search file
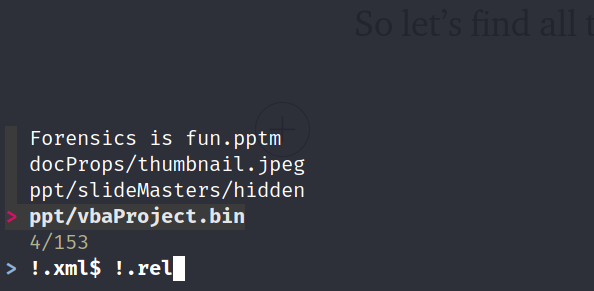
We’ve got the ppt/vbaProject.bin and ppt/slideMasters/hidden look really suspicious, let’s see what they contains.
cat ./ppt/vbaProject.bin
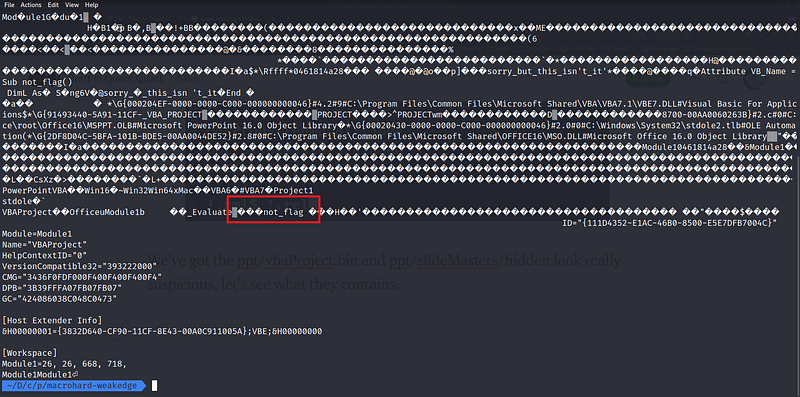
Hm… the .vba is actually the macro on which we inspected earlier, we can see the “not_flag” which showed earlier. It’s doesn’t contain the flag.
What about the ppt/slideMasters/hidden file?
cat ./ppt/slideMasters/hidden
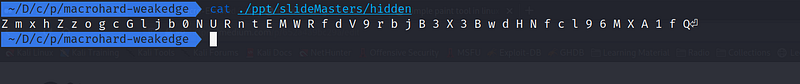
This is our last hope, but what is this? a bunch of random character? Maybe it’s the flag but it’s encoded. So i tried to decoded it in base64 and got the flag.
We got the flag: picoCTF{D1d_u_kn0w_ppts_r_z1p5}